The security architecture of a digital employment verification system is quite essential. It guarantees the following factors such as:
Integrity,
Confidentiality, and
Validity of the information shared between employers and workers.
Protecting these safety credentials requires tamper-proof technology with cryptographic, procedural, and technical measures.
What are Digital Signatures?
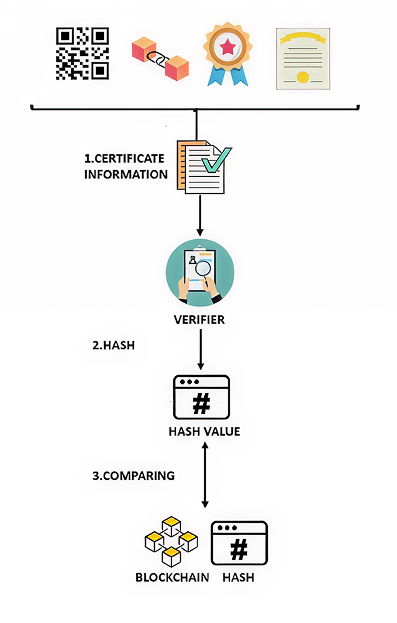
Asymmetric cryptography forms the basis of digital signatures. Here, a file gets signed with a private key. With a public key, the integrity and authenticity may then be confirmed. Both regulatory standards and the eIDAS regulation are included in this approach.
What Is the Process? Using the certificate data, a digital signature is generated and encrypted. In order to verify authenticity, the signature is compared with the original data.
It makes sure that a certificate’s contents can’t be changed. It also provides advanced security design.
Why do Certificates Need to be Tamper-Proof?
The need for a tamper-proof verification system is clear. Fraud cases are rising, legal disputes are growing, and communication costs are high. Digital certificates have many benefits.
• Protection Against Manipulation: They guard against the falsification of records and papers.
• Efficiency: Physical procedures are not required due to digital delivery and easy verification.
• Cost Savings: Digital certificates cut costs for printing, transporting, and storing.
Partners and recipients can trust that the documents are more authentic.
Get trustable employment verification done with Lystproof!
A Tamper-Proof Digital Employment Verification System’s Essential Elements
Let us see how the following factors outline the security and tamper resistance:
Blockchain
- Blockchain-based storage or audit logs secure records. They sign with cryptography. Once someone records their job status, they can’t change it without the public knowing.
- All modifications result in a new record instead of altering the previous one. Logs are time-stamped and append-only.
- This advanced security design prevents employment data from being tampered unnecessarily.
Digital Certificates and Signatures
- Employers digitally sign employment records through the use of public key infrastructure.
- You can check the document’s integrity and origin by using the public key to look at the signature.
- X.509 certificates are a reliable way to identify businesses.
- It confirms the data provider’s identity and shows the data is real and unchanged.
End-to-End Encryption (E2EE)
- This method encrypts all data, both in transit and at rest, using robust algorithms like TLS 1.3 and AES-256. Only authorized parties may access the decryption keys.
- It prevents illegal access or communication interception.
Zero-Knowledge Proofs
- Allows an employee to show specific employment conditions.
- For example, “employed in the last six months,” without sharing their full details.
- The significance of it reduces data leakage and improves privacy.
Authorization & Controls for Access
- Role-based access control (RBAC) and multi-factor authentication (MFA) allows only authorized users. They can view, request, or issue documents.
- Third-party verifiers may employ temporary, revocable access tokens.
- The significance of it restricts the exposure of data and stops internal misuse.
Accountability & Surveillance
- We record every request, access, and change with complete security. The logs are in tamper-evident formats. They are always checked for irregularities.
- It’s important because it prevents bad actors and offers forensic traceability.
Decentralization
- Decentralized identity systems include employment verification and self-sovereign identification (SSI) links.
- Authorized persons will issue credentials and confirm their validity on their own. But individuals keep control over their credentials.
- It enhances user privacy and control while reducing key points of failure.
Simplified Process Flow Example of a Digitally Verified Employment Data
1. The employer states, “We have employed Arun since January 2020.”
2. Keep it on a wallet or platform that you can verify through audit records or that has blockchain support.
3. The verifier needs proof. For instance, the bank requests employment verification.
4. The employee agrees, and they exchange the credentials with care.
5. Verifier confirms the identity of the issuer and verifies the signature.
6. An audit trail for the exchange is made.
Get Authenticated Employment Verification Done with Lystproof
Lystproof has a complete security architecture with safe and enhanced features. Lystproof covers the above mentioned security factors for an accurate employment verification system. You can use Lystproof for quick employment verification. Whether you’re an employer, employee, or admin, it takes less than 2 minutes.
Don’t go for paperwork when Lystproof is right at your hand?
Contact us today!